Do you suspect someone has hacked into your network? Maybe you’re experiencing strange Internet activity on your computer, or an unrecognized device is showing up in your Fing network scan. These can be signs that your network security was breached. Security breaches can be scary, but they can be solved and prevented. We’ll give you some pointers on how to do both.
Download Fing Desktop Download Fing App
What is a security breach?
A security breach is an event of unauthorized access to a network and its connected devices and data. Usually, the intruder is bypassing security with malicious intent. This involves accessing and stealing private data, causing disruption to systems, depriving authorized users access to their own devices, spying on user activity, etc.
Examples of security breaches are:
- Weak password abuse
It may surprise you, but the password 123456 still ranks highest on the most-used password list. With easy-to-guess passwords, hackers often don’t even need to hack the system in order to gain access. A password is always the first line of defense, so make sure it is strong. - Malware attack
One of the most common ways for cybercriminals to hack a network involves installing malware, which is software designed to perform various malicious tasks. There are many types of malware, including worms, viruses, Trojan horses, spyware, etc. Most of the time, malware is spread using phishing emails and fake websites. - Vulnerability exploit
With this kind of security breach an attacker gains access to a network by exploiting a vulnerability in that network. This can be a device that hasn’t been updated in a while, or just simply a coding error in a recent update from a software developer. - Evil Twin attack
Attackers imitate a Wi-Fi network by creating an Internet hotspot with an identical name. This lures in unsuspecting users who believe that they are connecting to their own Wi-Fi signal. The attacker can immediately monitor everything they do online. - Social engineering attack
The security breach here is a result of human interaction between the attacker and the victim that lead to the victim giving away sensitive information. This can happen over the phone, through email, in chat channels or apps. There are even instances where attackers used letters to trick people into divulging their data
How do you know if you’re hacked?
There are some signs that can point to a possible hack:
- Your passwords don’t work
- You’ve discovered unknown IP addresses on your network
- You see an unrecognized device on your network
- You don’t have control over your device
- You receive ransomware messages
- You’re often redirected to a strange website
What to do if you’re hacked?
The first thing to do is to secure your finances. Hackers most of the time are in it for the money. So, don’t make any online payments until the problem has been resolved. Call your bank and notify them that you’ve been hacked. A good idea is to have them freeze your accounts. While you’re at it, check your transactions at your bank to see if there are any that you don’t recognize. Once you’ve taken this important step, you can start by rectifying the problem as best you can.
Some quick-fix tips are:
- Try and change the passwords of your devices, your software, your websites. Prioritize the passwords of your wireless network (Wi-Fi) and your router admin page. Then prioritize your email client, because hackers are known to spread malware to contacts using your own email address and that may jeopardize your friends, family, and maybe even your company. Don’t forget to change security questions as well!
- Use a VPN (Virtual Private Network) for any Internet surfing you want to do for as long as your network is compromised. VPN services are a reliable way to keep out prying eyes because they essentially make a private network out of a public Internet connection. Consider using a VPN service even after the problem has been solved.
- If you don’t have access to a VPN service, at least use an Ethernet (cable) connection instead of your Wi-Fi. Ethernet is more secure. But don’t rely on it either.
- If you suspect your smartphone to be hacked, use your cellular network instead of your Wi-Fi.
- Scan your devices for malware using anti-virus software. It is possible that the security breach happened through malware, so scan your devices and remove any detected malware.
If you need help in solving a hack, you can always call your Internet service provider or you can report the hack to the police.
How do you prevent security breaches?
Protecting your home network is not difficult. Here are some pointers:
- The first line of defense are your passwords. Make sure that they are strong and regularly changed. Don’t just use the same password for every account either.
- Disconnect old devices that haven’t been updated in a while and avoid using them to connect to the Internet.
- Be mindful of phishing emails. Hackers are quite adept at imitating your suppliers, your government, even your friends and family. If something looks fishy, call the organization or person using their official number (not the one in the email) and ask if the email is legit.
- This may sound silly and very situational but be mindful of exes. After a breakup, you need to make sure that you close shared accounts and that your ex doesn’t have access to any of your passwords. It wouldn’t be the first time an ex was behind a security breach.
- Don’t access websites that have URLs that start with HTTP. Only access sites that use the HTTPS protocol.
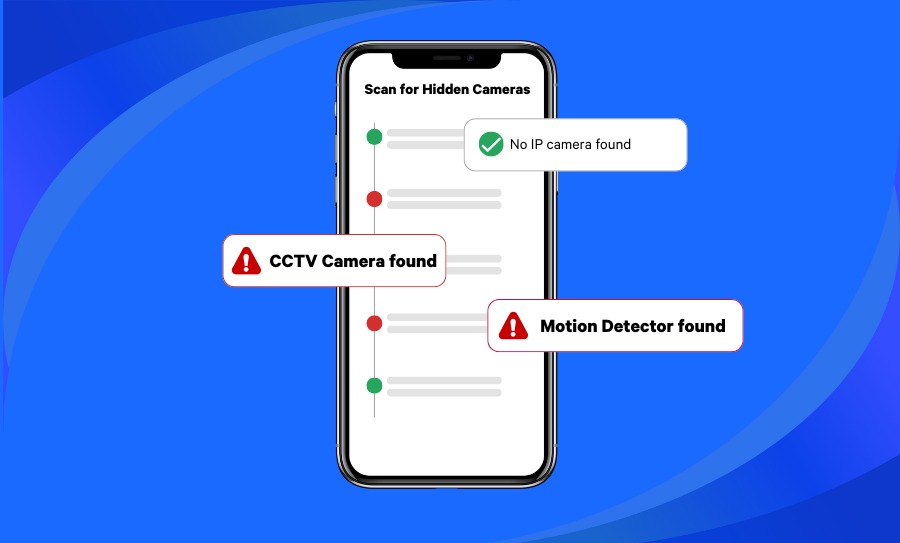
If you want to be thorough, use a network-monitoring app like Fing.
The advanced features of Fing App and Fing Desktop provide several security features that will help you to automatically track your network security and alarm you of any suspicious activity. For instance, our app can detect rogue devices and evil twin access points. It will tell you if you have any network vulnerabilities, or if you have any hidden cameras in your home. This allows you to proactively prevent security breaches, even when you’re not at home.